Setting up SSO
By default, Faros AI offers OAuth social login, allowing users to sign in with existing accounts from GitHub, Google, or Microsoft.
For enterprise customers, Faros AI also supports using Identity Providers (IdPs) to authenticate their users via SAML 2.0.
Availability: Enterprise Edition for users with Owner permissions
Identity Provider options include but are not limited to:
- Okta
- Azure Active Directory
- Google Workspace
- Custom IdPs using SAML 2.0 (please contact support)
- OpenID Connect (please contact support)
Setting up SSO with your IdP
This instructions are for SaaS deployments. If you have an on-prem deployment of Faros AI, the on-prem steps for setting up Okta are available here
Log in to Faros AI and then click on the profile icon in the lower left corner of the window. Click the SSO option under Tenant Settings (available to users with Faros Owner role only).
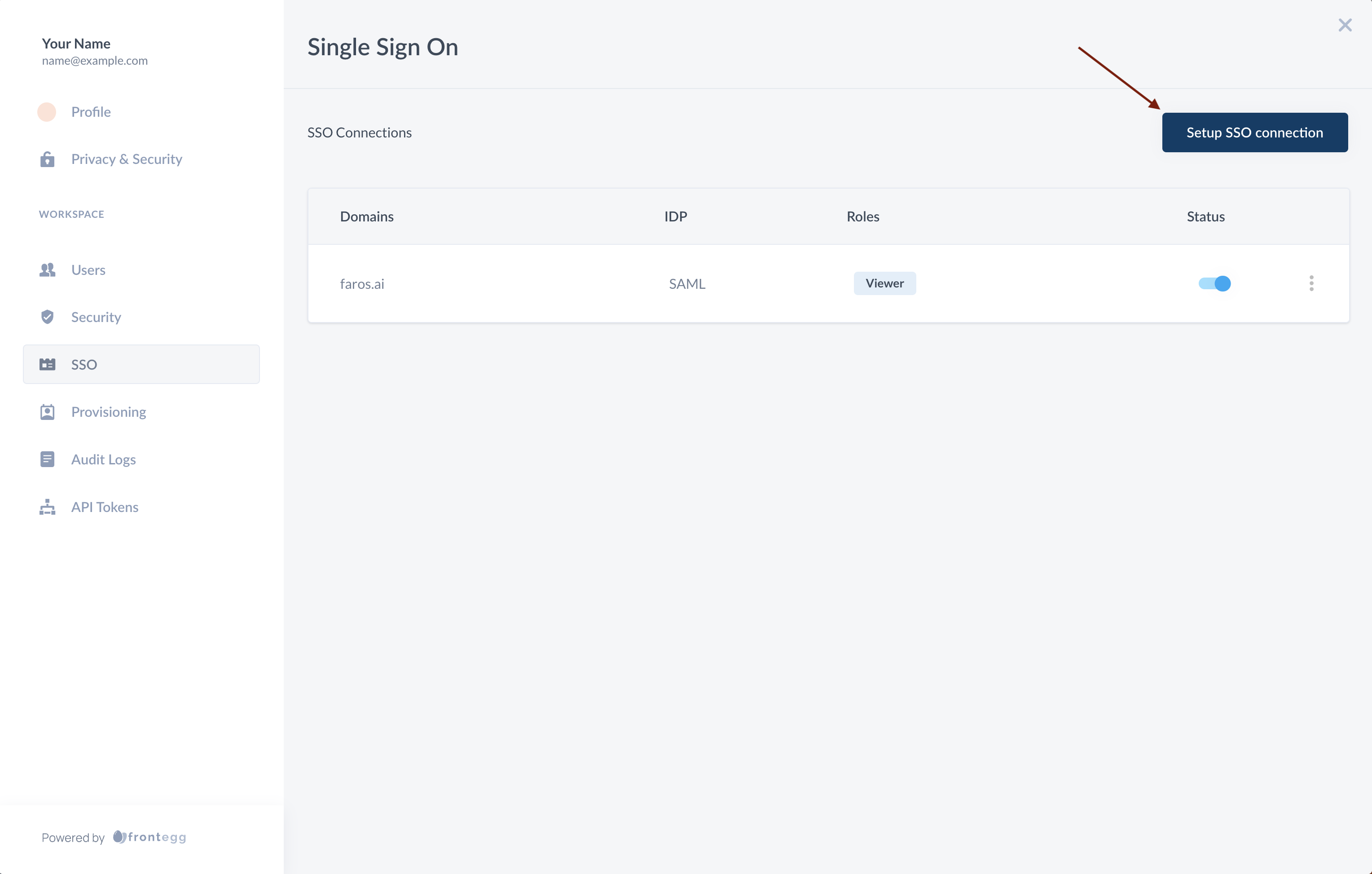
The Single Sign On page will allow you to edit previous SSO configurations or create new ones via the Setup SSO connection button.
Configuring a new SSO connection
Click the Setup SSO connection button to create a new connection
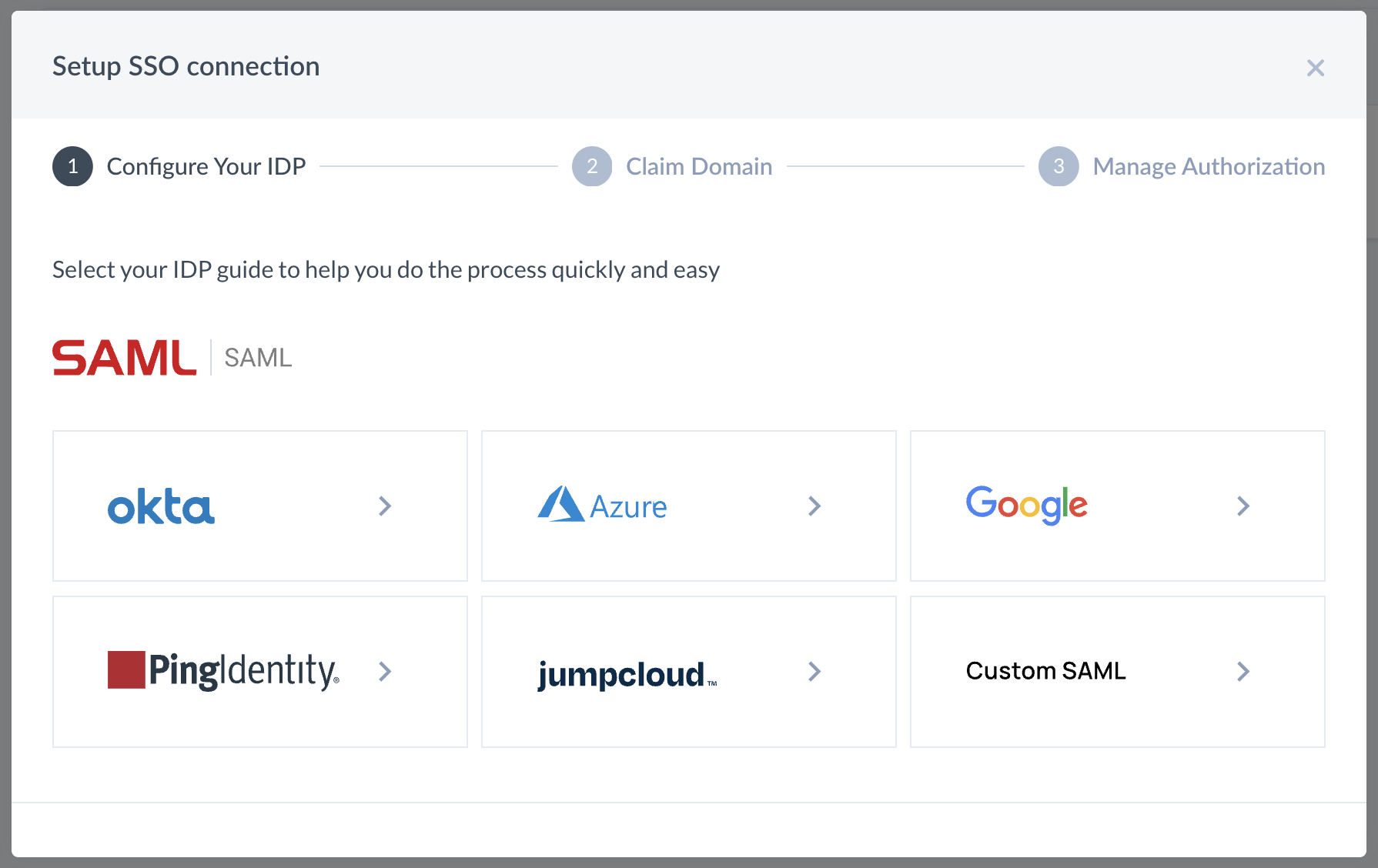
There are three steps to setting up a new connection.
- Configure Your IDP
- Claim Domain
- Manage Authorization
Configuring Your IDP
Please select an Identity Provider. After selecting an IdP, there will be detailed instructions specific to the selected provider. Please follow those instructions.
Here are the Faros AI logos, if you have the option to add an icon to your new integration:


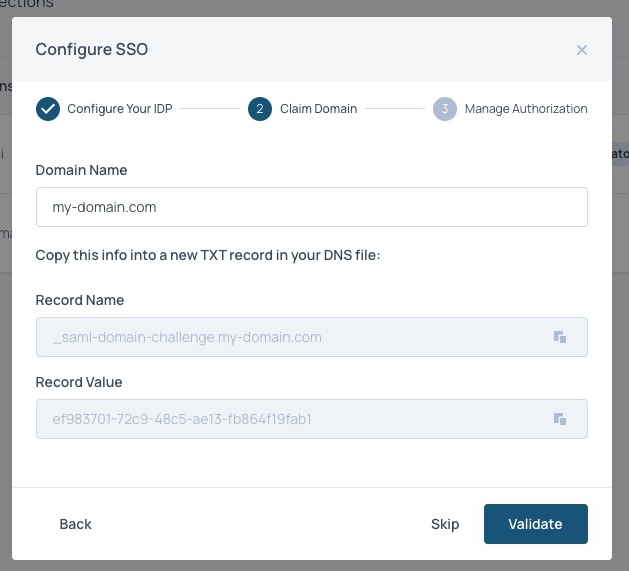
Claim domain
Please enter the domain of your emails. These will be the emails that can login to Faros AI via SSO. After clicking Proceed you will be provided a TXT record. Add it to your DNS. If are unable to do DNS-based validation of your domain, please contact support.
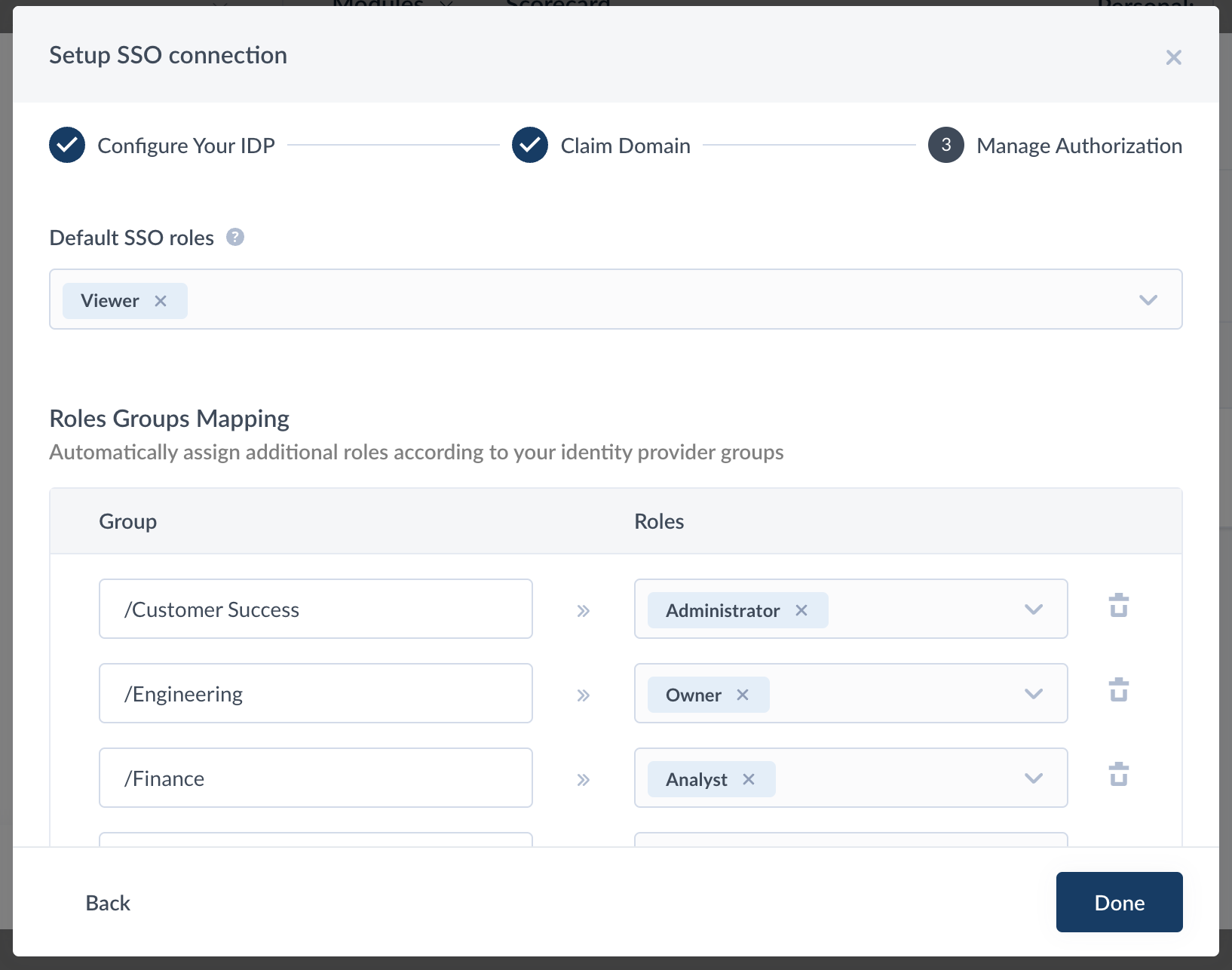
Manage Authorization
Enter your default SSO role. For more information on roles here. Default SSO roles are given to all users added to your Faros app. Usually, you will want to put Viewer or Analyst as the default role here - please use the role with the least permissions that you intend to use in your org.
Default SSO roles can be overwritten by the mappings in the Roles Groups Mapping section. The groups in this section will be defined within your SAML Provider.
- In Google, you will need to have the
groupsattribute configured in Google Workspace SAML - In Azure, the
groupsattribute should be configured in Azure AD -> Faros AI application -> Single Sign-On -> SAMLAttributes & Claimssection populated withusers.groupsvalue. - In Okta, you will need to have Group Attributes configured in Okta.
Updated 5 months ago
To automate user (de)provisioning within Faros AI consider setting up SCIM user provisioning
